
For a long time, I kept all of my account passwords in an encrypted file on my computer. While millions of people were turning to online password-management services, I was reluctant, fearing the calamity that might ensue were such a service to be hacked, exposing the sensitive information of perhaps millions of people.
Finally, in April of 2021, I decided to take the plunge. While continuing to maintain my offline password file as a backup, I started using an online service, and even started advising my clients that it seemed safe to do so, if they followed some essential security practices — starting with creating very secure master passwords for their online password vaults that would not be guessable, not use patterns commonly used in passwords, and not be used as the passwords for anything else.
Then came the multiple breaches of security at LastPass, one of the most popular password-management services.
In August, LastPass alerted customers that someone had broken into a portion of their system that is physically separated from where customers’ information is stored, and that customers’ information itself was secure. More recently, the company reported that, using resources gleaned from that August breach, malicious actors had gotten ahold of some customer information — names, partial credit-card numbers, and other data — but not any stored password information.
Finally, on December 22, the company sent an alert to customers notifying them that an update had been posted in the LastPass CEO’s blog. In that blog, the CEO reported that the hackers have indeed accessed backup copies of users’ password “vaults,” the files storing their passwords.
The user IDs and passwords in those files, along with any secure notes stored there, are strongly encrypted, but that doesn't mean the problem isn't severe. As LastPass personnel confirmed to me, some portions of those files were not encrypted — including the Web addresses of services used by those customers. So, for example, while the hackers cannot readily access the log-in data for sites used by LastPass customers, they can compile a list of those sites — a digital “map” showing which online services each customer uses. Paired with the stolen customer data previously reported and other information that can be found on the Internet, this means that accounts included in those LastPass vaults are at risk if they themselves don’t have strong passwords. People who have used the same password on multiple sites are especially vulnerable.
Moreover, it’s very likely a large percentage of LastPass users haven’t followed the best practices in creating the master passwords that unlock their password vaults. If the hackers can guess those master passwords, then every account in that customer‘s LastPass vault is accessible.
LastPass says that if you have a good master password for your LastPass vault, it would take millions of years to decipher it. But determined hackers can set up networks of thousands of computers to work on the problem, possibly reducing “millions of years” to a few years, or even several months. It is likely that a substantial number of the stolen password vaults will be cracked in the next couple of years (and some of the most vulnerable will be accessed much sooner).
Customers Are Vulnerable Immediately
Even if the hackers can access only the portions of the LastPass files that are not encrypted, there are many ways that data can be used maliciously. Obviously, someone who has stored passwords to illegal or unsavory Web sites in LastPass will be very unhappy that their use of those sites is exposed, even if their account log-ins remain secure. And if the person has easy-to-guess user IDs and passwords on any of those sites, they may be at risk of having their accounts broken into.
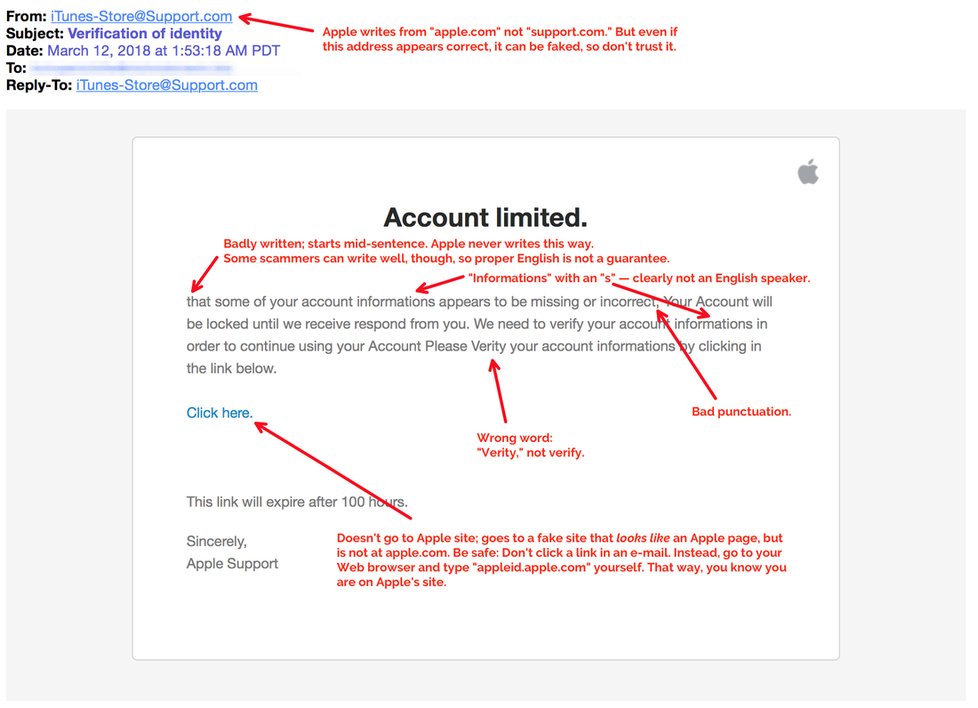
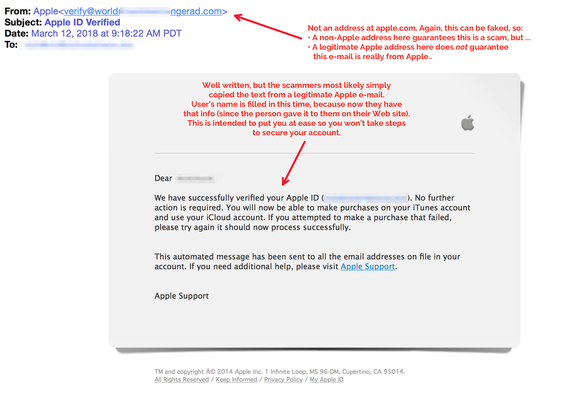
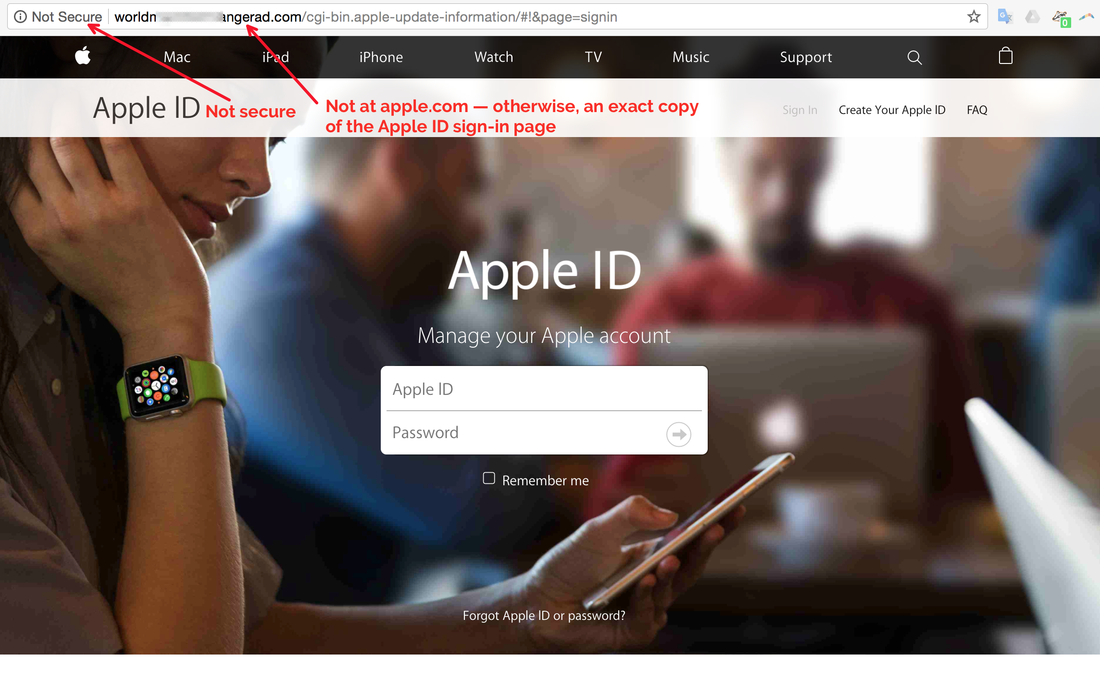
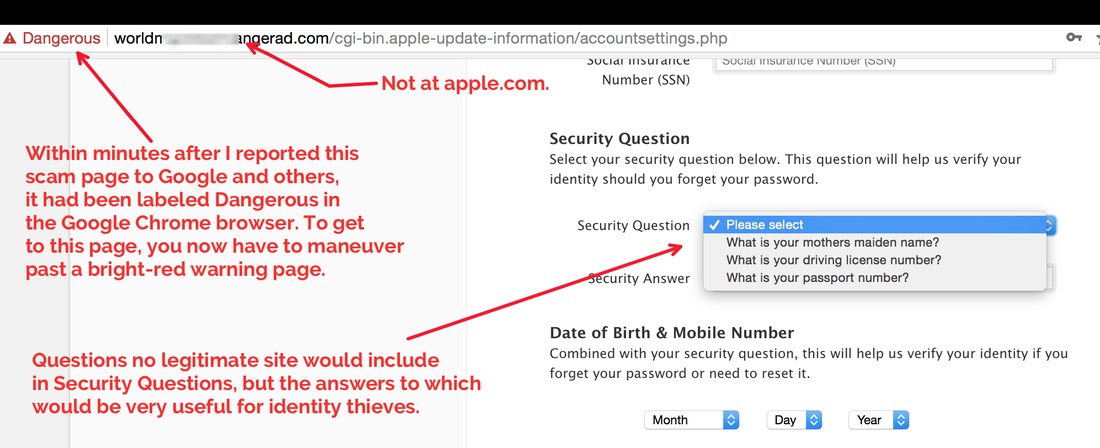
But perhaps the most immediate danger is that the data can be used for "social engineering" attacks. This means criminals can call, text, or email a person, using information gleaned from their LastPass account to make them sound legitimate, and trick people into divulging passwords or other data. For example, a person could call you and say that they are calling from your Wells Fargo bank to report that your Netflix, San Diego Gas & Electric, and Humana Health Plan payments aren't going though, and they need a credit card number from you to fix the problem. They sound legitimate to you — after all, they know you have Netflix, SDG&E, and Humana. It doesn’t occur to you that they learned about those accounts from your stolen LastPass vault.
I am not, for now, recommending people switch from LastPass to other password-storage services, mainly because I think any password service might be vulnerable to such attacks; in fact, the steps LastPass has taken since this happened may make LastPass less vulnerable to future hacks than other services. Rather, after reading several reports in the tech press about this incident, I have stopped recommending using any online password-storage system, at least if you can set up a secure password vault on your own devices or offline (e.g., in a paper notebook). I can advise clients on how to do that.
Steps Everyone Should Take
Meanwhile, the following five steps are crucial (for everyone, not just LastPass users):
 Graphic by Pete Linforth via Pixabay Graphic by Pete Linforth via Pixabay (1) MOST IMPORTANTLY: Make it a rule to never give out log-in IDs, passwords, answers to security questions, account numbers, or any other sensitive information to anyone who contacts you, unless you first requested the contact. Even then, a legitimate call will almost never include requesting your full credit-card number, full account number, or your full Social Security number. Be aware that these callers can sound very persuasive: I've been taken in by them myself in the past. (2) If you are a LastPass user, look through your LastPass vault to review what someone can learn about you by knowing which Web sites and services are included there, and how you can defend yourself against misuse of that information. Whether you use LastPass, another password service, or no password service, be aware that if someone contacts you who knows things about you, such as that you use certain online services, they may have learned that illicitly — don't trust them just because they know a lot about you. Similarly, if someone contacts you who claims to be connected to a friend of yours, and “proves” it by mentioning private information about that friend, keep in mind that they may have stolen that private information. (3) If you are continuing to use LastPass, change the master password to your password vault, so updated information it contains won’t be accessible to the hackers if they should be able to figure out your master password using the data they’ve already stolen. If you use any password service, change your master password for that service it if isn't highly secure — 12 characters or more, and not guessable (doesn't include your birthday, Social Security number, street name or address, pet name, school you went to, common words, etc.). Some rules for strong passwords are provided here. (4) If you have insecure passwords on any of your online accounts, change them. If you are a LastPass customer, change the passwords on your most critical accounts (banks, credit cards, utilities, government log-ins, etc.) within the next few weeks, and all other accounts over the next few months. It’s a pain, but not nearly so much of a pain as having your money or identity stolen. Keep in mind there is no such thing as an “unimportant” online account — nearly any account can be used to pose as you and trick your friends, for example. (5) If you re-use the same password on multiple accounts, change them to unique passwords. That way, if someone steals or guesses your password on one account, they won't be able to access others. With the recently revealed LastPass hack, criminals now know which sites each person uses, making it easier to find all of a person's online accounts. |
More About This Incident
- LastPass Confirms Hackers Stole Its Password Vaults — What You Should Know (HotHardware.com)
- LastPass Password Vaults Stolen By Hackers — Change Your Master Password Now (Forbes)
- How To Delete Your LastPass Account … and Move Elsewhere (Tom’s Guide) [Note: As I wrote above, I don’t think other online password managers are likely to be immune from similar attacks in the future]
























 RSS Feed
RSS Feed