There’s a new kind of brute-force attack, and it doesn’t involve clubs, nunchucks, or dynamite. The target is a function within WordPress that goes by the alphabet-soup name “the XML-RPC service.” Attackers use that service to find a site manager’s password. From there, they can do anything they want: break the site, send out spam, conduct identity theft, even launch attacks on other Web sites. If you have a WordPress site, you may be vulnerable (most are).
Fortunately, there is protection against this kind of attack.
Awhile back, hackers broke into the WordPress site of one of my clients and created a set of hidden pages that tricked users into entering their personal information (passwords, etc.), then transmitted that information to the hackers. We found and deleted those pages and the programming that ran them, and we changed all the passwords related to that site, but we needed to also ensure the hackers wouldn’t find a way in again and start their criminal activity all over.
The site’s hosting company wanted to sell us an expensive security package. Our WordPress expert advised that a free alternative, Wordfence, would be just about as good, while saving our client significant money.
So, what is this thing called a "brute-force attack"? How does this relate to the XML-RPC service? How do I protect my site from it? And if I don’t have a WordPress site, am I still vulnerable?
A “brute-force attack,” in Internet terms, is where automated software tries to guess your log-in password, making hundreds, thousands, or millions of attempts in rapid succession. The software may simply go through various combinations of letters, numbers, and words; a more-sophisticated version may scan your Web site looking for clues (e.g., a particular name appears repeatedly, so the software guesses you’ve incorporated that name into your password).
The new “XML-RPC” attack uses a function within the WordPress system to vastly multiply the number of guesses the hackers can make while reducing their chance of detection. Basically, it allows the attacker to send many guesses in a single command, so many more attempts can be tried in a short period of time. Moreover, some protection software might not notice how many attempts are being made, because hundreds or thousands can be “bundled” together and the software sees only the number of bundles, not what’s inside of them. (A somewhat-technical explanation of how this attack uses XML-RPC may be found here.)
One way to protect against this particular type of attack is to disable the XML-RPC function. However, this function may be needed by your site’s plug-ins (software that extends the functionality of WordPress, such as Contact Form 7 to create feedback forms on your site), so XML-RPC should be disabled only if you are sure you don’t need it.
Another way to defend against this kind of attack is with software that will block the hackers’ log-in attempts. After our client’s site was hacked, we installed a WordPress plug-in called Wordfence. Wordfence stops users from logging in after a certain number of failed attempts. It also monitors where the attacks originate and will block specific Web addresses or even countries. (Our client’s site has been attacked frequently from France. Since the only people allowed to manager her site are in the U.S., we are fine blocking log-in attempts from abroad.) These are all customizable settings.
Wordfence protects against the XML-RPC attack because it isn’t fooled by the attackers’ effort to hide how many log-in attempts they are making. It “sees” 1,000 attacks whether they come via 1,000 individual commands or are all hidden within a single XML-RPC command.
If you would like us to ensure that your WordPress site is protected against this kind of attack, let us know. We’ll see whether you already have protection installed, and whether it guards against XML-RPC attacks. If necessary, we can install and set up Wordfence. The cost would be under $100.
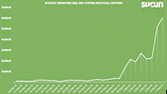
The number of XML-RPC attacks is rising dramatically, and probably will continue to do so: As hackers gain access to more WordPress sites, they use them to launch attacks against still more sites. The chart below shows statistics compiled by Internet security firm Sucuri as of a week ago. There were 60,000 attacks on Oct. 7 alone. (Each attack can represent hundreds or thousands of log-in attempts.)
Make sure your site doesn’t become a target — and that it doesn’t get used to make even more victims.
What about non-WordPress sites? Continued below ↓
Some tips for secure passwords:
- Longer is better. Minimum 8 characters (including letters, numbers, and punctuation); Edward Snowden says that’s too short; some others say at least 12. Each additional character multiplies the number of possibilities and lengthens the amount of guessing time needed.
- Avoid dictionary words, names, or information that’s easy to find about you (birthday, address, phone number, school you attended...). If you can Google your name and the information and find it, don’t use it in passwords.
- Use a combination of UPPERCASE and lowercase letters, as well as numbers and symbols.
- If you want to be able to remember your password, instead of words or names, use the first initials. Instead of “ThisIsMyPassword28934” (or “This Is My Password 28934” if you are allowed to use spaces), try “TiMP28934!” (Where “28934” is not something easy to track down. You used to live in area code 289, and moved away when you were 34; that won’t be too obvious.)
- Don’t use the same password for multiple sites. I don’t use memorable passwords, and I have a different password for every site or account. I keep them in a secure file that itself is encrypted with a strong password. I have set up similar systems for clients, and could help you with that too.
More about secure passwords may be found here. A secure-password generator and software for securely storing passwords may be found here.
More about brute-force attacks may be found here.

 RSS Feed
RSS Feed